TL;DR – if you really want to take ownership of protecting your personal data, you really should read this. Really.

This latest evolution of at blogging for me has been more fun than in the past. The coding and technology around hosting my own blog has become much more robust than it was previously. This gives me time to actually compose meaningful content. When my brain is cooperating. My reasons for wanting to host my own blog are a whole different conversation that I may visit at a later date. Eight days my blog has been live. I am already seeing brute force attempts to access the dashboard. One of the nice features that I was able to implement is security around unauthorized attempts to gain access to my framework. This new tool tracks what happens and takes steps to mitigate them without my direct intervention. Leaving me more time to study, explore and compose entries. Typically, one of the penetration methods used involves default or common credentials known as a “dictionary attack”. Brute force attacks are usually next but can vary based on the style of the attacker. Brute force can be automated but requires a lot of processing power at times. This is where good password practices can dig a robust moat. Over the years I have witnessed and participated in a good number of discussions around passwords. There are several schools of thought around passwords that I won’t cover here. There is a general underlying theme though. Here’s my take on passwords and why I follow these exigencies.
Passwords should follow the 8-4 rule. The 8 is the number of characters. The 4 is the requirements for character population. Mine typically are anywhere from 20-128 characters But I’ll cover that reasoning later (and how I manage them).
- It should be a minimum of 8 characters long.
- It should contain at least 1 upper case letter.
- It should contain at least 1 lower case letter.
- It should contain at least 1 number.
- It should contain at least 1 non-standard character.
In addition:
- Never use personal information.
- Randomize it whenever possible.
- Never use the same password for different accounts
Again, I will come back around to how I manage this level of complexity in my passwords later.
This may seem familiar to you. Especially if you work in a managed corporate environment. While aggravating, that prompt you get every 2-4 months to change your company password is there as a measure to protect access to company resources. Getting into this habit with your personal accounts is beneficial to protecting your personal data. Anyone who has had their identity stolen can attest to the horror and difficulty around recovering what you’re able while learning to build the moat necessary to help protect yourself. But why? The short answer is because brute force attacks can be automated. Yes, I know there should be other things in play to work with this and help with prevention. But we are discussing taking ownership. Unless you are the architect of your own system, those additional protections are usually not at your discretion. The rules that this level of password complexity bring elevates the math to a level that, when used with additional layers of protection in conjunction with your password, can go a very long way to protect you from experiencing a personal data breach. But like I said, we are discussing this in the context of personal ownership.
Let’s discuss the numbers. There are 26 letters in the English alphabet. So, if we follow the 8-character minimum using only lower-case letters, that gives us over 208 billion possibilities. Which sounds like a lot. Until you consider that a typical consumer grade processor of 1.8Ghz can perform roughly 1.8 billion operations per second. So that means the computer can create all of the possibilities in under 2 minutes. I know there are other factors to consider. We will factor in other time variables and complexities later. Including what GPT can possibly mean for this. Quite simply, the basic math is frightening enough.
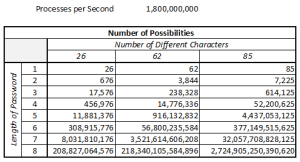
Changing to include capitol, lower case and numeric values brings us to 62. That 62-character count takes us to the dizzying value of 218.3 trillion possibilities. Now we’ve extended the simple aggregated calculation time to 35.28 hours. That can be an acceptable moat when you’re working with a system that has reasonably good information security SLAs in place. For me personally that moat isn’t deep enough yet. Now add in the typically available non-standard characters found on a QWERTY keyboard. Our character count is now 85. This makes the time to solve for the entire set of possibilities just under 18 days.
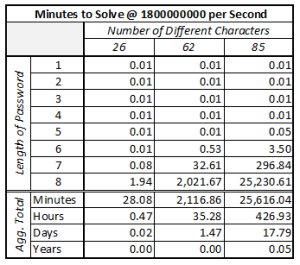
This is where we consider some factors that will reduce that number. It is common for automated systems to work sequentially. Think along the lines of For Next and Do While loops. If my complex password is P@ssw0rd, it is going to occur roughly 62% of the way through that 85-character set. Which takes a major cut into my 18 days and reduces it to just under 11 days. If my attacker is using a decently configured system that has two 1.8Ghz processors, that time has now been reduced to just over 5 days. So now you understand why I use 20–128-character passwords depending on the limitations and need for the particular application. Before you come @ me, I know there are other factors that can extend or reduce the time. I am still trying to keep this digestible for non-information technology or infosec folks.
So now that I’ve brought your focus on to just why those simple passwords you may love are bad for you, let’s talk about how to manage the passwords you will collect using these complexity rules. The easiest from a password management perspective? Don’t touch the internet. This also means you’ll probably have to drop from the grid entirely and start living in a protected commune somewhere that is separated from current society. The alternative is a password manager. There are things that make password managers good. In the interest of operational security, I won’t share with you what password manager I use. I will tell you what I look for when choosing one.
A good password manager…
- …does not store your passwords unencrypted.
- …has the option to autodelete your device local or cloud storage password database after a definable number of failed attempts.
- …can be installed on multiple platforms (phone, tablet, laptop, desktop, server)
- …can be integrated with AD or utilize ACLs (this is more of an enterprise level requirement).
- …requires MFA or multifactor authentication to log in to. this can include but is not limited to voice, text, email and or application-based authentication.
- …has login sessions that expire after a definable period.
- …has remote management capability to allow for deactivation on remote devices.
In summary, get a password manager. Yes, there are systems that can be put in place to further reduce risk. But we are talking about personal ownership, right? Stop using your kids’, birth months combined your anniversary date as your password. Because GPT technology is going to make this whole thing even more complicated. It’s not far-fetched to envision a GPT model that uses OSInt to refine the data and create customized hybrids brute force and dictionary attacks even more detailed than they have been to date.
Now that I’ve painted a beautifully grim picture of what we face, I wish you a thoughtful day.
